Nothing screams out good network engineer than some proficiency in Wireshark. In this post we will go through what Wireshark is, how it can help you, and some basics.
What is Wireshark?
Wireshark is a packet capture utility available for Windows and Mac OSX (along with ports for Linux). This allows you to capture the network traffic between two devices.You can download Wireshark from https://www.wireshark.org/.
Getting started with Wireshark
I am using UNetLab here, which offers great Wireshark integration.Check this link for Wireshark integration on OSX.
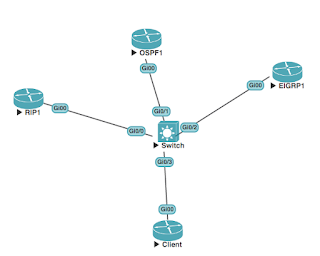
We have a simple topology, running RIP, OSPF and EIGRP. We will be capturing the traffic coming in and out of Client:
With this set up we should see some good traffic!
The configurations are below:
RIP1(config)#int gi 0/0 RIP1(config-if)#ip add 10.10.1.120 255.255.255.0 RIP1(config-if)#int lo0 RIP1(config-if)#ip add 120.120.120.120 255.255.255.255 RIP1(config-if)# RIP1(config-if)#router rip RIP1(config-router)#network 10.10.1.0 RIP1(config-router)#network 120.120.120.120 RIP1(config-router)# OSPF1(config)#int gi 0/0 OSPF1(config-if)#ip add 10.10.1.88 255.255.255.0 OSPF1(config-if)#no shut OSPF1(config-if)#int lo0 OSPF1(config-if)#ip add 88.88.88.88 255.255.255.255 OSPF1(config-if)#ip ospf network point-to-point OSPF1(config-if)# OSPF1(config-if)#router ospf 1 OSPF1(config-router)#network 10.10.1.88 0.0.0.0 area 0 OSPF1(config-router)#network 10.10.1.88 0.0.0.0 area 0 OSPF1(config-router)# EIGRP1(config)#int gi 0/0 EIGRP1(config-if)#ip add 10.10.1.89 255.255.255.0 EIGRP1(config-if)#no shut EIGRP1(config-if)#int lo0 EIGRP1(config-if)#ip add 89.89.89.89 255.255.255.255 EIGRP1(config-if)# EIGRP1(config-if)#router eigrp 1 EIGRP1(config-router)#network 10.10.1.89 0.0.0.0 EIGRP1(config-router)#network 89.89.89.89 0.0.0.0 EIGRP1(config-router)# Client(config)#int gi 0/0 Client(config-if)#ip add 10.10.1.10 255.255.255.0 Client(config-if)# Client(config-if)#int lo0 Client(config-if)#ip add 10.10.10.10 255.255.255.255 Client(config-if)#ip ospf network point-to-point Client(config-if)# Client(config)#router rip Client(config-router)#network 10.10.1.0 Client(config-router)#network 10.10.10.0 Client(config-router)#no auto Client(config-router)# Client(config-router)#router ospf 1 Client(config-router)#network 10.10.1.10 0.0.0.0 area 0 Client(config-router)#network 10.10.10.10 0.0.0.0 area 0 Client(config-router)# Client(config-router)#router eigrp 1 Client(config-router)#network 10.10.1.10 0.0.0.0 Client(config-router)#network 10.10.10.10 0.0.0.0 Client(config-router)# Client(config-router)#The interfaces are currently shutdown on RIP1, OSPF1, EIGRP1 and Client. So we will turn on Client's interface first, and can start capturing the data:
Client(config-router)#int gi 0/0 Client(config-if)#no shut Client(config-if)#Once Wireshark starts showing siome packets, we can bring up the other interfaces:
RIP1(config)#int gi 0/0 RIP1(config-if)#no shut OSPF1(config)#int gi 0/0 OSPF1(config-if)#no shut EIGRP1(config)#int gi 0/0 EIGRP1(config-if)#no shutAfter we have some traffic, we can stop Wireshark by clicking on the red square.
We should see something similar to this:
You can download this file from:
https://docs.google.com/uc?export=download&id=0BwJlq_qocwWbLS1CdXRiYklRZmc
We can see traffic for EIGRP, OSPF and RIP (amongst other traffic). But like this it is hard to really dig into anything in particular. So, we can filter our traffic.
Filtering in Wireshark
At the top of the Wireshark window is a box that says "Apply a display filter..." If we click in that, we can enter something to filter on.Click in the box and type in rip. You should see the box go green, along with an option for "ripng". We are just interested in RIP for the moment, so just press return:
If we wanted to look at just the OSPF traffic, we can change the filter to "ospf":
Similarly for EIGRP:
If the box is green, the query is clean (to paraphrase Ghostbusters)!
What is in a packet?
Wireshark can tell us all about the packets that are sent between hosts.If we select a packet (such as packet 12), we can see the Frame data, and this includes the encapsulated data:
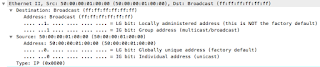
We then have the Ethernet data - this is our MAC information, telling us the layer-2 destination and source addresses. We can tell that this is a broadcast packet as the address is ff:ff:ff:ff:ff:ff, and the hardware address it originated from (50:00:00:01:00:00). It also tells us that it is an IP packet (0x0800):
We then have the layer-3 information:
Here we can see that layer-3 IP addresses. The source is 10.10.1.120 (RIP1) and the destination is the broadcast address 255.255.255.255. We also have Quality of Service data, by way of the Differentiated Services Field data. We then have the underlying protocol used for the traffic, which is UDP.
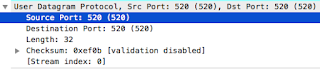
The UDP data comes next:
Here we have the source and destination port (520).
Finally, we have the RIP data:
This is a great way of seeing what the traffic is actually made up of.
More useful Wireshark stuff:
We can limit down the data displayed to a particular host, and this includes the host as both the source and the destination, using a filter of "ip.addr == <ip address>":The Internet is a pretty large place, so sometimes IP addresses are not much help to us and we need to use the DNS name instead. We can, Wireshark will do DNS lookups, we just have to enable it:
We can also track an entire conversation between two hosts, such as an HTTP call.
You can download the Wireshark file here.
In it's raw state, we can have more information than we need:
We cannot filter on HTTP traffic though, in this instance, but we can filter based on the port number (80). We can used the filter function (by clicking on "Expresson" next to the filter bar) to build our filter, which is useful if we do not know the syntax:
This has now filtered the RIP traffic out, leaving us with just the traffic on port 80:
We can use the captured data to rebuild, well, pretty much anything, from pictures to entire web pages. All we need to do is "follow the stream":
This brings up a new window with the reconstructed data:
This is exactly what we see from the RIP1 router:
RIP1#telnet 10.10.1.10 80 Trying 10.10.1.10, 80 ... Open get HTTP/1.1 400 Bad Request Date: Thu, 04 Feb 2016 20:55:29 GMT Server: cisco-IOS Accept-Ranges: none 400 Bad Request [Connection to 10.10.1.10 closed by foreign host] RIP1#As you can see, Wireshark is a great tool, and it does not take much time to learn the basics.
It is an essential tool in networking.