When studying for any network certification, there are a couple of choices. You can either purchase all the physical equipment, rent some racks, or go virtual.
In this post we will weigh up some of the pros and cons of each approach.
This said, this can be a costly method, and the routers and switches can become useless as the exams change, and you can end up with a garage full of 1U paper weights. The bits and bobs you pick up from eBay will probably not be suitable for SmartNet, and therefore you won't be able to update them (legally).
Pros: Less change of errors compared to virtual devices. Realism.
Cons: Cost, limited usability lifetime
Pros: Less initial monetary outlay
Cons: Costs can easily mount up, less options for configuration
We could run VMWare ESXi server, which is a hypervisor, but this would then require a second machine to manage the virtual machines.
The second option is to run a normal desktop, and then run the virtualization software within it. The options are VMWare Player (free), VMWare Workstation, or VMWare Fusion. The CPU must support virtualization, here Intel is much preferred, especially where UNetLab is concerned (so look for VT-x support). VirtualBox is not a preferred hypervisor as it (currently) lacks nested virtualization support.
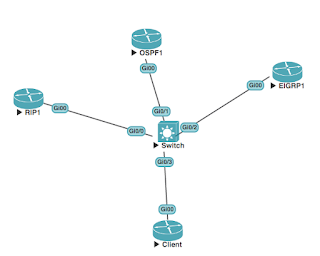
We also need a fairly decently specced machine. Ideally we need to give the network VM about 8GB of memory, meaning that the host machine will need about 16GB of memory. A VM with 8GB will allow you to run a fairly decent sized network (between 768Mb to 1024Mb for switches, and 512Mb for routers), so you could run a handful of switches and still have room for a number of routers.
This then allows us to build the networks we need, when we need, and can add images (device images) as and when we can find them, so the equipment does not become outdated (unlike purchasing physical equipment).
The biggest downside to this is the initial cost. Whilst the cost of a PC with 16GB or more can be quite high, once the costs of this are compared to purchasing physical equipment, or renting a rack, the cost is actually quite reasonable, especially when calculated over the lifetime of the study period, or average lifetime of the hardware (three years). This is one of those times when it's better to invest early, so the rewards can be reaped quicker.
The more memory you can get, the better. 16Gb will allow enough for the host operating system (Windows or Mac OSX), and the virtual machine.
Zoostorm, whilst not the well-known brand, do a good range of affordable PCs, which are pretty decently-specced. Brand names, such as Dell are probably more advisable, but slightly more costly. It is worth shopping around. Whilst eBay is good, second-hand equipment may not last as long as you need it to, but there are some good bargains to be had.
where do a wide range of suitable Linkage.
Virtual networks, for a home lab, are definitely the way forward. It allows much more control and expandability, whilst keeping costs at a sensible level.
Pros: Complete control, can easily add new devices, won't become out-dated
Cons: Initial costs can be high
In this post we will weigh up some of the pros and cons of each approach.
Physical network equipment
Nothing will beat the real thing. It is going to be closer to the actual environment and there will be less issues compared to virtualization. There is also the geek pride associated with having a room chock-full of esoteric blinking lights from a rack full of routers and switches. The initial outlay can run to a few hundred moolah.This said, this can be a costly method, and the routers and switches can become useless as the exams change, and you can end up with a garage full of 1U paper weights. The bits and bobs you pick up from eBay will probably not be suitable for SmartNet, and therefore you won't be able to update them (legally).
Pros: Less change of errors compared to virtual devices. Realism.
Cons: Cost, limited usability lifetime
Rent a network rack
Renting equipment can be suitable, but you can be bound to pre-designed topologies, so you lose the ability to design your own networks (unlike having your own physical equipment, or a virtual setup). Depending on the vendor, and the number of hours you need to buy (and remember this could be over a number of years), the cost again can run into the hundreds.Pros: Less initial monetary outlay
Cons: Costs can easily mount up, less options for configuration
Run a virtual network
The last option we are going to discuss is running a virtual network. for this we need a base operating system and/or some virtualization software.We could run VMWare ESXi server, which is a hypervisor, but this would then require a second machine to manage the virtual machines.
The second option is to run a normal desktop, and then run the virtualization software within it. The options are VMWare Player (free), VMWare Workstation, or VMWare Fusion. The CPU must support virtualization, here Intel is much preferred, especially where UNetLab is concerned (so look for VT-x support). VirtualBox is not a preferred hypervisor as it (currently) lacks nested virtualization support.
We also need a fairly decently specced machine. Ideally we need to give the network VM about 8GB of memory, meaning that the host machine will need about 16GB of memory. A VM with 8GB will allow you to run a fairly decent sized network (between 768Mb to 1024Mb for switches, and 512Mb for routers), so you could run a handful of switches and still have room for a number of routers.
This then allows us to build the networks we need, when we need, and can add images (device images) as and when we can find them, so the equipment does not become outdated (unlike purchasing physical equipment).
The biggest downside to this is the initial cost. Whilst the cost of a PC with 16GB or more can be quite high, once the costs of this are compared to purchasing physical equipment, or renting a rack, the cost is actually quite reasonable, especially when calculated over the lifetime of the study period, or average lifetime of the hardware (three years). This is one of those times when it's better to invest early, so the rewards can be reaped quicker.
Suitable PCs to use as a virtualization platform
As a general rule of thumb, look for an Intel-based processor, one which supports VT-x, this is required for virtualization. The more cores it has, the more you can give to the virtual machine, and the better it will run.The more memory you can get, the better. 16Gb will allow enough for the host operating system (Windows or Mac OSX), and the virtual machine.
Zoostorm, whilst not the well-known brand, do a good range of affordable PCs, which are pretty decently-specced. Brand names, such as Dell are probably more advisable, but slightly more costly. It is worth shopping around. Whilst eBay is good, second-hand equipment may not last as long as you need it to, but there are some good bargains to be had.
where do a wide range of suitable Linkage.
Virtual networks, for a home lab, are definitely the way forward. It allows much more control and expandability, whilst keeping costs at a sensible level.
Pros: Complete control, can easily add new devices, won't become out-dated
Cons: Initial costs can be high